Analysis of Extremist and Terrorist Groups on Twitter

We perform a longitudinal analysis of online social behavior of ISIS as an extremist and terrorist group on Twitter, and compare it with extremist Twitter activities of the Islamic Regime in Iran, as an authoritarian regime.
Publications
- Younes Karimi, Analysis of Extremist and Terrorist Groups on Twitter, Ph.D. Thesis, publicly availabe through Penn State libraries.
- Younes Karimi, Anna Squicciarini, Peter K. Forster;
Longitudinal Dataset and Analysis of Twitter ISIS Users and Propaganda, published in the Springer-Nature Social Network Analysis and Mining (SNAM) Journal, the Special Issue on Collective intelligence on Web and Social Media, 2024. - Younes Karimi, Anna Squicciarini, Peter K. Forster, Kira M. Leavitt;
A Longitudinal Dataset of Twitter ISIS Users (arXiv preprint | Dataset) - Priyadarshini Murugan, Younes Karimi, Anna Squicciarini, Chirstopher Griffin;
Modeling Longitudinal Behavior Dynamics Among Extremist Users in Twitter Data, IEEE BigData, 2021 Paper | Slides | Presentation
The recent rise in social media use has many benefits, such as more connectivity and access to more diverse information, communities, and resources for demonstrating support for various causes. However, social media platforms have led to many unexpected negative phenomena: misinformation, disinformation, and cyberbullying. Worryingly, Islamist extremist groups like the Islamic State (ISIS) and authoritarian regimes such as the Islamic Regime in Iran (IR) have embraced social media to contact their target audience directly and recruit new members, undermine or threaten their rivals, and spread propaganda messages. My goal in this dissertation is to explore the Twitter activities of these two groups and propose automated approaches for identifying their supporters and propagandistic tweets.

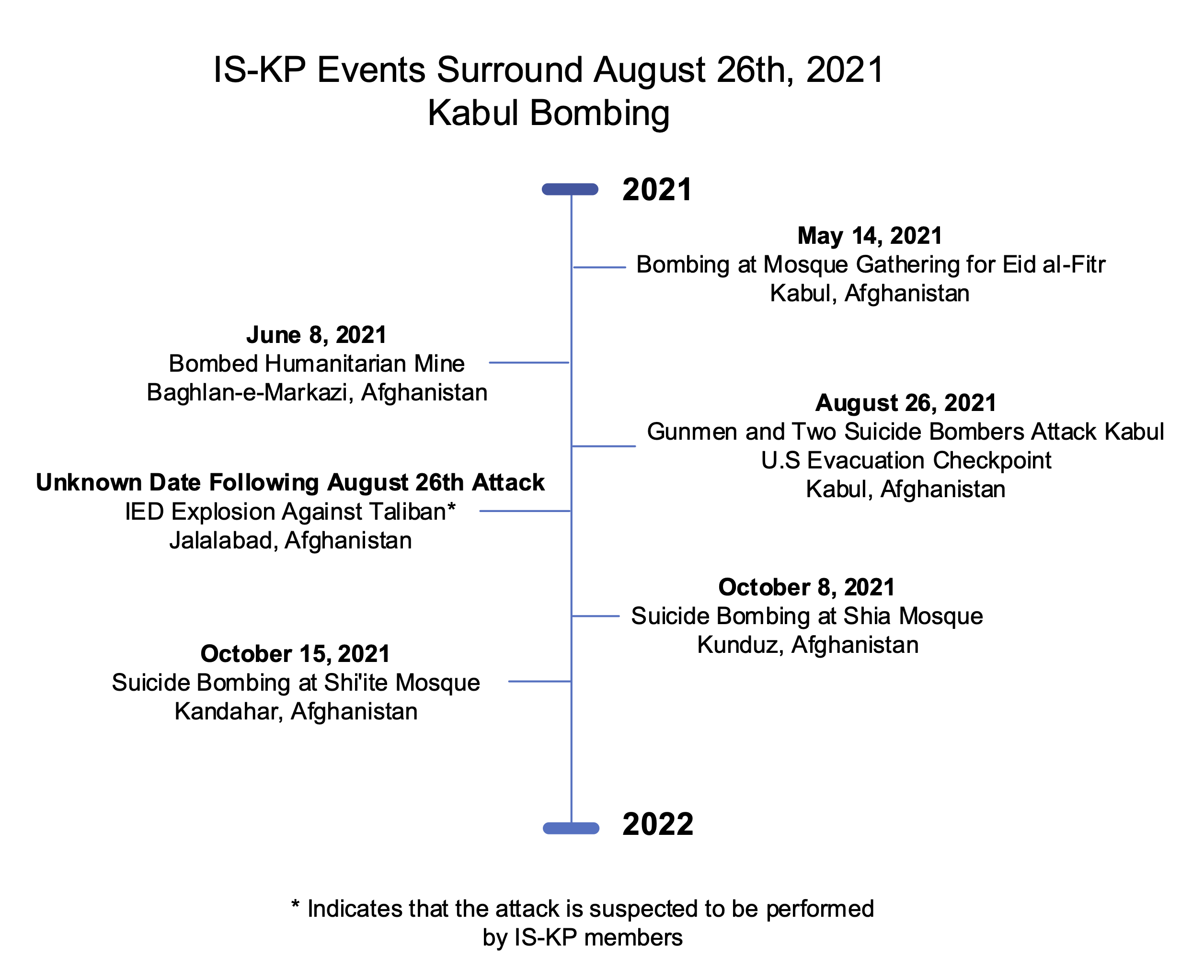
Although ISIS was driven out of its last territory in Syria and its physical caliphate collapsed in 2019, recent terrorist attacks and incidents in various areas such as Central Africa, and recently designated terrorists by the Department of State signify the presence and growth of ISIS affiliates. Yet, once under scrutiny, their whereabouts have been less known and studied since then.
In this paper, we aim to re-open this line of investigation to further our understanding of the recent ISIS online presence. We collect and analyze a longitudinal dataset of tweets from potential ISIS affiliates and an existing dataset of ISIS Twitter activities around 2015--when Twitter cracked down on many ISIS accounts. We build a user classifier to identify ISIS supporters on Twitter. We further investigate different types of content and topics used by known ISIS accounts and compare these attributes among ISIS and its potential affiliates. We also identify messages that gained abnormal attention and support and presumably were used to spread propaganda and influence and manipulate the online community. Finally, we build and evaluate an image classifier using the Residual Network pretrained image classification models to categorize the photos attached to the candidate propaganda tweets of ISIS and identify the major themes in those media files.
This work was funded by the National Science Foundation under grant number 1909255:
Extremist behavior in large scale datasets
We present a large longitudinal dataset of tweets from two sets of users that are suspected to be affiliated with ISIS. These sets of users are identified based on a prior study and a campaign aimed at shutting down ISIS Twitter accounts. These users have engaged with known ISIS accounts at least once during 2014-2015 and are still active as of 2021. Some of them have directly supported the ISIS users and their tweets by retweeting them, and some of the users that have quoted tweets of ISIS, have uncertain connections to ISIS seed accounts. This study and the dataset represent a unique approach to analyzing ISIS data. Although much research exists on ISIS online activities, few studies have focused on individual accounts. Our approach to validating accounts as well as developing a framework for differentiating accounts' functionality (e.g., propaganda versus operational planning) offers a foundation for future research. We perform some descriptive statistics and preliminary analyses on our collected data to provide deeper insight and highlight the significance and practicality of such analyses. We further discuss several cross-disciplinary potential use cases and research directions.
This work was funded by the National Science Foundation under grant number 1909255:
Extremist behavior in large scale datasets
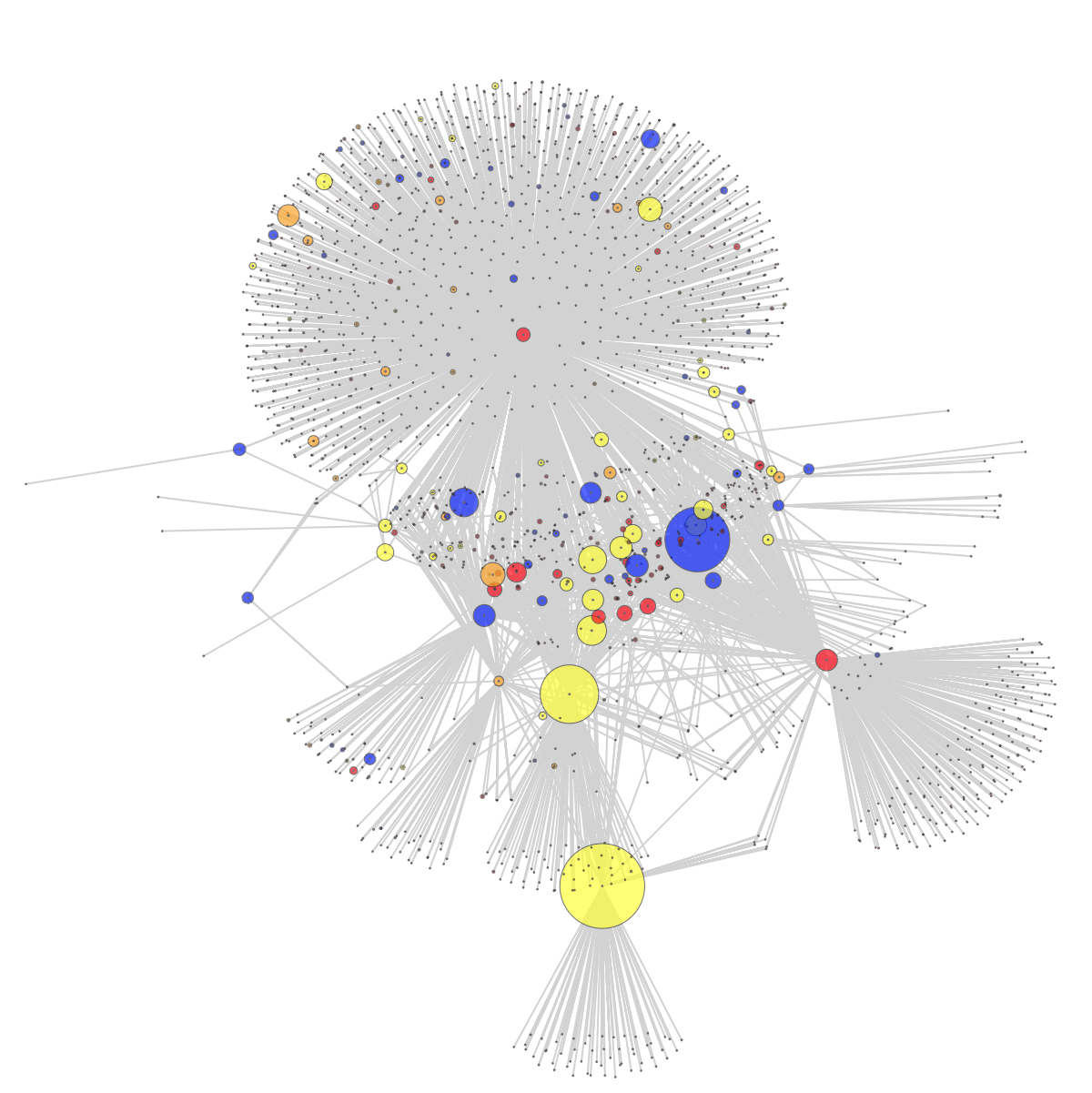
We use a dynamical systems perspective to analyze a collection of 2.4 million tweets known to originate from ISIS and ISIS-related users. From those users active over a long period of time (i.e., 2+ years), we derive sequences of behaviors and show that the top users cluster into behavioral classes, which naturally describe roles within the ISIS communication structure. We then correlate these classes to the retweet network of the top users showing the relationship between dynamic behavior and retweet network centrality. We use the underlying model to formulate informed hypotheses about the role each user plays. Finally, we show that this model can be used to detect outliers, i.e. accounts that are thought to be outside the ISIS organization but seem to be playing a key communications role and have dynamic behavior consistent with ISIS members.